Optimize Your Reach with Cloud Services Press Release Techniques
Wiki Article
Enhance Information Protection With Trusted Cloud Solutions
In today's interconnected electronic landscape, the importance of boosting data security with relied on cloud services can not be overemphasized. By delegating information to respectable cloud providers geared up with innovative protection procedures, organizations can strengthen their defenses versus cyber risks and make sure data privacy.Value of Data Security
Making sure robust data safety and security measures is critical in today's digital landscape to safeguard delicate info from unauthorized accessibility and cyber risks. With the rapid growth of information generation and storage, organizations deal with raising obstacles in protecting their beneficial assets. Data violations not only lead to monetary losses but also damage an organization's credibility and deteriorate consumer depend on.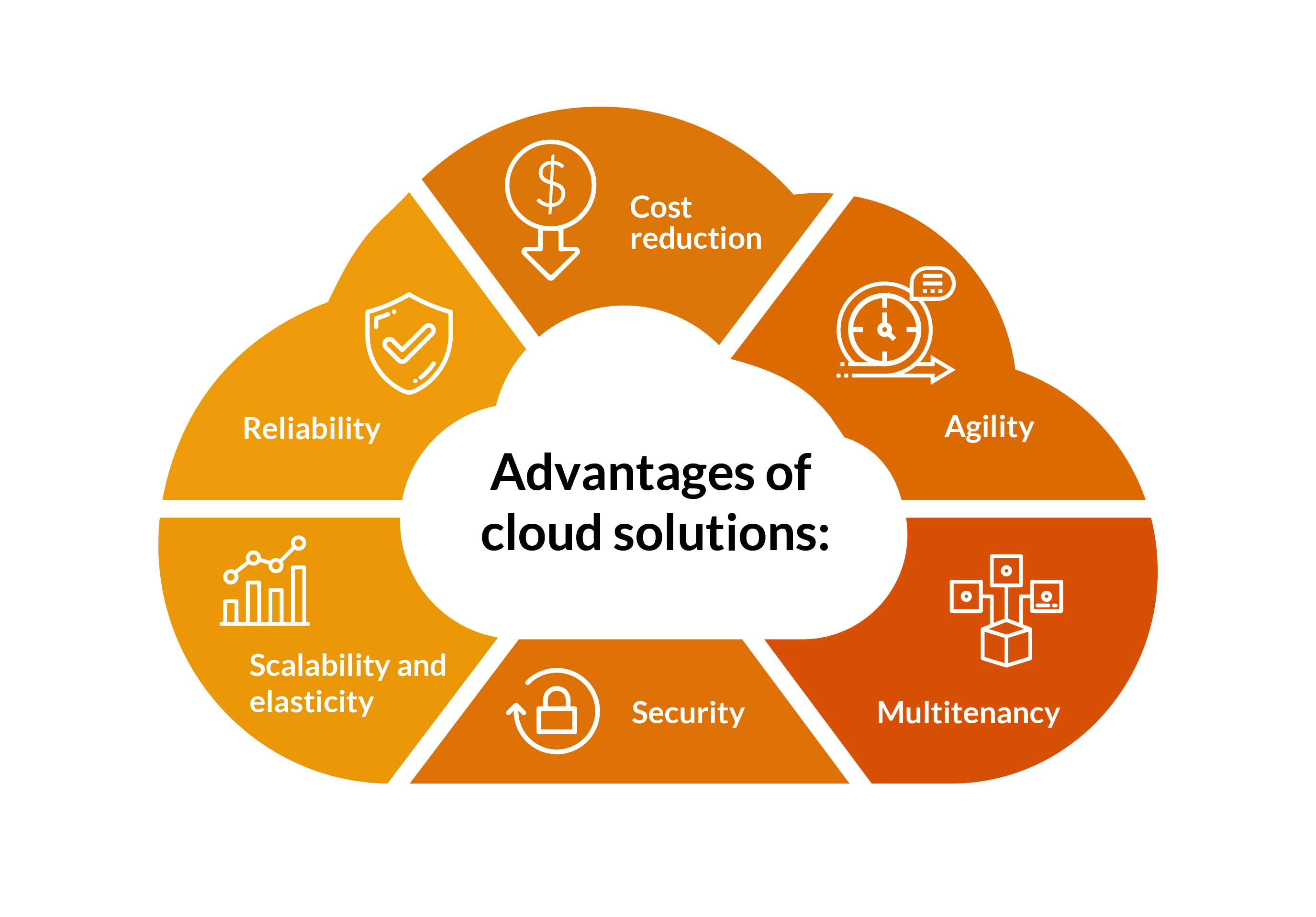
In the present period of remote work and cloud computing, the relevance of data safety is additionally amplified. Cloud solutions supply scalability, cost-efficiency, and versatility, yet without adequate safety and security actions, they can pose considerable threats. Consequently, companies should prioritize information safety when embracing cloud solutions to stop data violations and promote the stability of their procedures.
Advantages of Relied On Cloud Providers
Offered the rising importance of data safety and security in the electronic landscape, comprehending the benefits of trusted cloud solutions comes to be necessary for organizations aiming to fortify their data protection approaches. Trusted cloud solutions supply many benefits that can boost data safety steps. To start with, these solutions offer durable security procedures, guaranteeing that data is firmly kept and transmitted. This file encryption helps protect against unapproved access, decreasing the risk of information breaches.Moreover, trusted cloud services provide reliable backup and calamity recuperation options, making sure data availability even in case of unanticipated cases. This dependability is important for preserving business connection and lessening data loss. Overall, the advantages of relied on cloud services add considerably to strengthening information safety methods within organizations.
Trick Functions of Secure Cloud Solutions
Applying durable safety and security steps is essential in guaranteeing the honesty of information kept and transmitted with cloud remedies. Secure cloud options supply vital functions that help protect sensitive details. File encryption plays a critical function in safeguarding data by inscribing it to make it unreadable without the correct decryption secret. This ensures that also if unauthorized customers access to the data, they can not decode its contents. In addition, secure cloud remedies offer multi-factor verification, requiring customers to offer numerous types of confirmation prior to accessing the data. This additional layer of security helps protect against unapproved access, even if login qualifications are compromised. Another vital feature is routine protection updates and patches that help attend to any vulnerabilities and reinforce the system versus potential risks. In addition, secure cloud services frequently include sophisticated hazard discovery mechanisms that continuously keep an eye on for suspicious activities and prospective breaches. These attributes jointly add to a much more protected cloud environment, instilling confidence in individuals relating to the security of their data.Finest Practices for Data Security
To fortify data safety and security in cloud environments, adhering to best techniques for data defense is vital. File encryption plays an essential function in protecting delicate info saved in the cloud. Carrying out encryption systems, both at rest and en route, ensures that information is muddled to unauthorized customers even if it is obstructed. Gain access to control is one more essential method for data security. By applying strict accessibility controls, organizations can limit that can view, edit, or remove information, minimizing the risk of unauthorized accessibility. On a regular basis backing up data is likewise a basic aspect of data defense. In case of data loss or a security breach, having up-to-date back-ups makes it possible for swift healing without endangering valuable information. Furthermore, surveillance and bookkeeping data access and usage help in discovering any type of suspicious tasks quickly. By complying with these finest methods for information protection, organizations can improve their data safety stance in the cloud environment.Choosing a Dependable Cloud copyright
Picking a reliable cloud provider is a crucial decision for companies looking for to improve their data security actions. When selecting a cloud supplier, a number of crucial elements should be taken into consideration to make sure dependability. Organizations should examine the provider's safety and security procedures, including information encryption, accessibility controls, and compliance certifications. A reliable cloud supplier should have durable security procedures in position to secure information against unapproved access and cyber dangers.Additionally, organizations must evaluate the company's uptime and integrity performance history. Downtime can have significant ramifications for service procedures and data access, so choosing a company with a proven performance history of high uptime is important. Moreover, companies must consider the scalability and flexibility offered by the cloud service provider to accommodate future growth and altering service requirements.
Last but not least, evaluating the company's client support services is critical. In the event of any kind of concerns or protection violations, well-informed and responsive customer assistance can make a substantial distinction in mitigating dangers and guaranteeing timely resolutions. By very carefully thinking about these aspects, organizations can pick a reliable cloud provider that fulfills their data safety needs effectively.
Conclusion
To conclude, leveraging trusted cloud solutions is vital for improving data security in today's electronic landscape. By executing robust file encryption protocols, progressed danger detection capacities, and reputable back-up services, companies can efficiently safeguard beneficial information and mitigate risks of information breaches. Picking a reputable cloud provider and following best practices for data protection are essential actions in maintaining information integrity and making certain comprehensive security versus cyber risks.By entrusting information to respectable cloud service providers equipped with advanced protection measures, companies can fortify universal cloud Service their defenses versus cyber threats and guarantee information discretion. Organizations should prioritize information safety and security when embracing cloud solutions to protect against data breaches and support the stability of their operations.
Offered the climbing importance of data safety and security in the digital landscape, understanding the advantages of relied on cloud solutions becomes imperative for organizations aiming to strengthen their information security strategies.To strengthen data safety and security in cloud atmospheres, sticking to ideal techniques for information security is extremely important. By adhering to these best techniques for information security, organizations can improve their data security posture in the cloud environment.
Report this wiki page